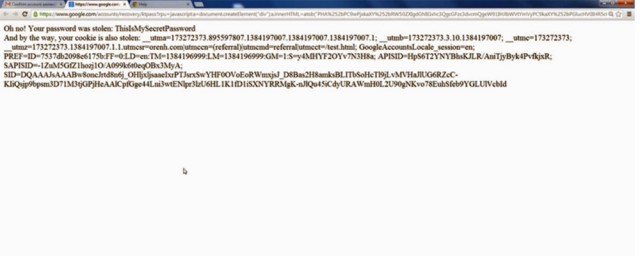
Google engineers have squashed several high-impact security vulnerabilities in the company's account recovery system that enabled attackers to hijack user accounts.
A proof-of-concept attack that exploited the bugs required a victim to click a booby-trapped link leading to Google.com contained in a spear phishing e-mail. Behind the scenes, the link briefly redirected to an attacker's website even as it opened a legitimate password-reset page on Google. When a victim clicked on the link while logged in to the targeted Gmail account, the attacker site also performed a cross-site scripting attack. The Web application equivalent of a Jedi mind trick, the two exploits sent both the password entered by the victim and the authentication cookie used to access the account to the attacker's website.
"It's a clever attack," Jeremiah Grossman, CTO of Web-application security firm WhiteHat Security, told Ars. "There's elegance and simplicity." The exploit developer "did a lot of work behind the scenes to make the attack simple. This is what we're meant to do in a browser on Gmail. When we see links, we're meant to click on them."
Coming up dandelions
A Google representative told Ars that the vulnerabilities came to the company's attention on November 9 when security researcher Oren Hafif privately reported them. Google engineers fixed them on November 20. A day later, Hafif posted this blog post describing how the exploit worked. Here's a video that shows the attack in action:
Redirection, cross-site scripting, cross-site request forgery, and SQL-injection vulnerabilities are to websites what dandelions are to suburban lawns. Even sites maintained by experienced and highly vigilant Web developers are likely to suffer from these Web-application bugs. Frequently, they are little more than an embarrassment for website developers, since in isolation they often have few if any practical consequences for security. But as Hafif's exploit demonstrates, these very common bugs can provide highly effective ways for attackers to breach an otherwise impenetrable fortress, especially when the bugs are exploited in unison.
"If I told you to think of the most sensitive features (security-wise) in a Web application, you would probably say-Login," Hafif wrote in his blog post. "Well if your definition of 'Login' does not include password recovery, then it would definitely be the second one. This means that password recovery is often in the center of attention for attackers-and for security professionals."
What makes Hafif's attack so effective is its ability to seamlessly stitch together exploits for at least two very subtle bugs. Based on Hafif's blog post, it appears that the Google account recovery system, or possibly the entire Google.com domain, suffered from a redirection vulnerability that allowed Web requests directed at Google sites to end up at a different site of the attacker's choosing. Hafif's account also described a cross-site scripting bug that allowed him to bypass routine security checks carried out by Google Web apps. Hafif said he will be receiving a financial reward under Google's bug bounty program, although he didn't say how much Google is paying him. Google thanked him.
There's no telling how long the vulnerabilities existed until Hafif came along and discovered them. The episode is a graphic example of the value derived from bug bounty programs sponsored by Google, Mozilla, Facebook, and a growing number of other companies. Even assuming that Google paid the maximum $10,000 available for this type of exploit under its bounty program, it was a bargain compared with the cost of hiring outside auditors or, worse, suffering widespread exploits against users.
news by November 23, 2013 at 01:53AM
{ 0 comments... Views All / Send Comment! }
Post a Comment